Powershell Detection/Security Features and Bypass

PowerShell has several features designed to improve the security of your scripting environment.
• System-wide transcription
• Script Block Logging
• Module Logging
• Antimalware Scan Interface (AMSI)
• Constrained Language Mode
System-wide transcription
If enabled, all the commands and their output of the PowerShell session will be logged on the local machine.
Enabling System-wide transcription:
Simply type start-transcript and your session will be recorded in your home folder. After quitting PowerShell, the recording stops. You can also stop recording manually by running Stop-Transcript
The log file content will be stored at
C:\Users\test\Documents\PowerShell_transcript.DESKTOP-T2S9MRG.RGgNXQOv.20220110043314.txt
What does the log file look like?
Script Block Logging
It records blocks of code(unobfuscated) as they are executed by the PowerShell engine.
Two modes:
1. Automatic mode - By Default enabled, logs based on known suspicious keywords
2. Verbose mode- logs everything
Enabling Script Block Logging:
Open the Local Group Policy Editor and navigate to Computer Configuration > Administrative Templates > Windows Components > Windows PowerShell > Turn on PowerShell Script Block Logging
Checking the logs on Windows:
Open Event Viewer and navigate to the following log location: Applications and Services Logs > Microsoft > Windows > PowerShell > Operational
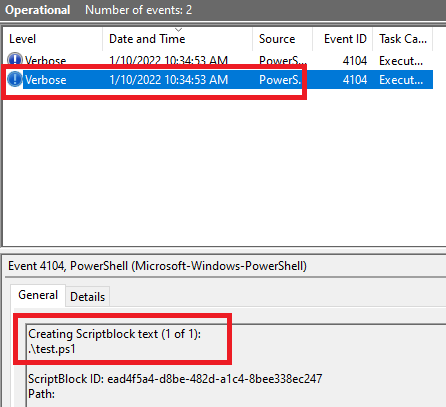
Script block logging events are recorded in EID 4104.
Script code:
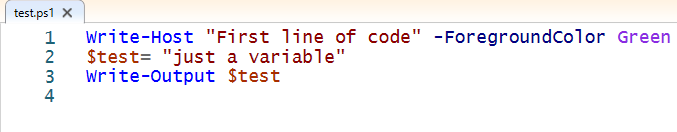
./test.ps1
Running test.ps1 created 2 events
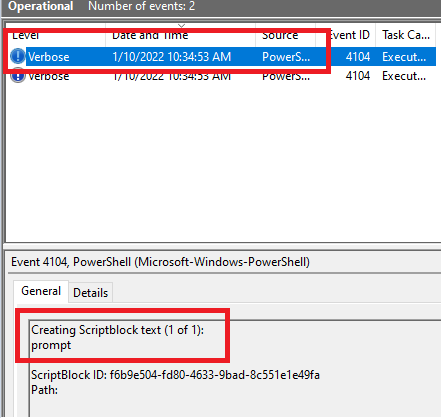
Module Logging
Module logs show how PowerShell commands/code are executed in PowerShell, capturing tons of useful information like variable initialization and other useful data not captured by any of the other logs. Module log data will be logged as each command is processed, creating individual events for each one.
Enabling Module Logging:
Open the Local Group Policy Editor and navigate to Computer Configuration > Administrative Templates > Windows Components > Windows PowerShell > Turn on Module Logging
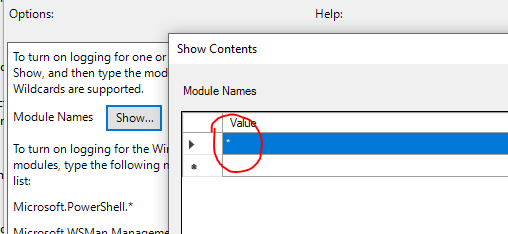
In the Module Names window, enter * to record all modules. Module logging events are written to Event ID (EID) 4103.
Script:
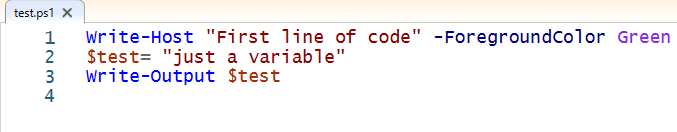
./test.ps1
Running test.ps1 created 3 events
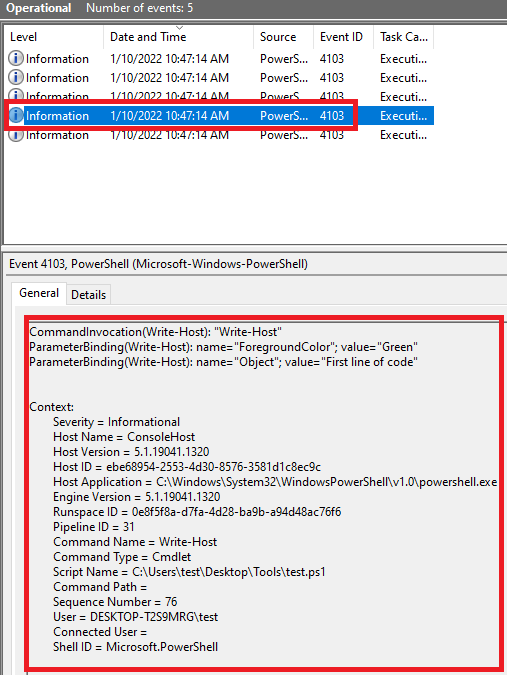
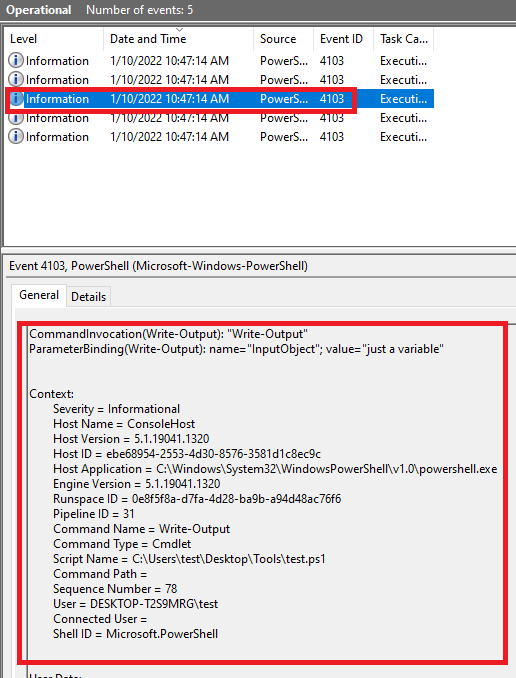
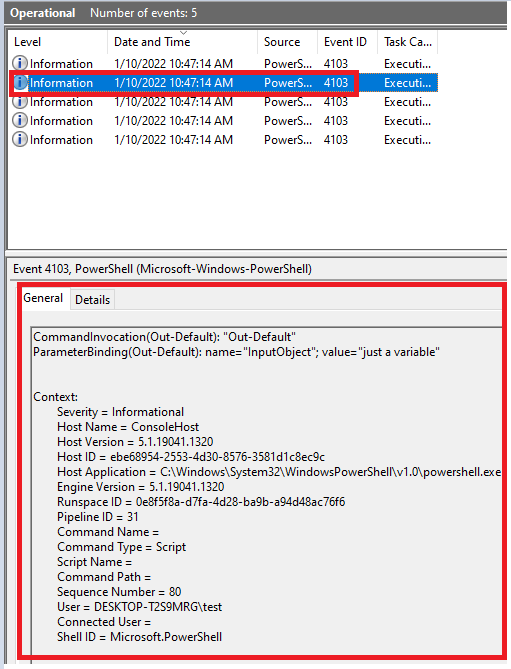
AntiMalware Scan Interface(AMSI)
When a user executes the PowerShell script, AMSI pops in (AMSI.DLL is loaded) and it passes it (using the function "AmsiScanBuffer()" ) to registered Antivirus. AV checks if any of its signatures match with the powershell script.
The AV installed on the system needs to support AMSI in order for the code to be scanned.
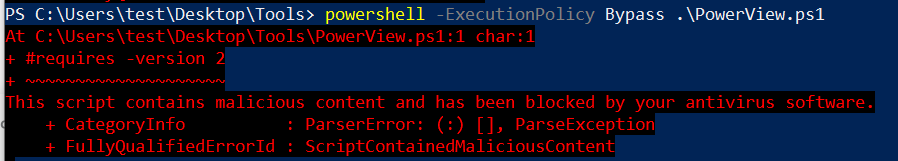
Powershell Detection/Security Features Bypass
Invisi-Shell (https://github.com/OmerYa/Invisi-Shell)
Invisi-Shell bypasses all of Powershell’s security features (ScriptBlock logging, Module logging, Transcription, AMSI) by hooking .Net assemblies. The hook is performed via CLR Profiler API.
We need 3 files:
1. InvisiShellProfiler.dll - https://github.com/OmerYa/Invisi-Shell/blob/master/build/x64/Release/InvisiShellProfiler.dll
2. RunWithPathAsAdmin.bat - https://raw.githubusercontent.com/OmerYa/Invisi-Shell/master/RunWithPathAsAdmin.bat
3. RunWithRegistryNonAdmin.bat - https://raw.githubusercontent.com/OmerYa/Invisi-Shell/master/RunWithRegistryNonAdmin.bat
Exit the PowerShell using the exit command (DON’T CLOSE THE WINDOW) to allow the batch file to perform the proper cleanup.
Reference: