Rotating Host IP Address for Pentesters/Red Team

There are many use cases why you need to rotate your IP address, some use cases on top of mind:
IP-based rate limiting bypass
After making 3 wrong authentication attempts, application was blocking me for 24 hours
Testing/Bypassing IPS/WAF rules
Hide/generate traffic during the attack simulation campaign
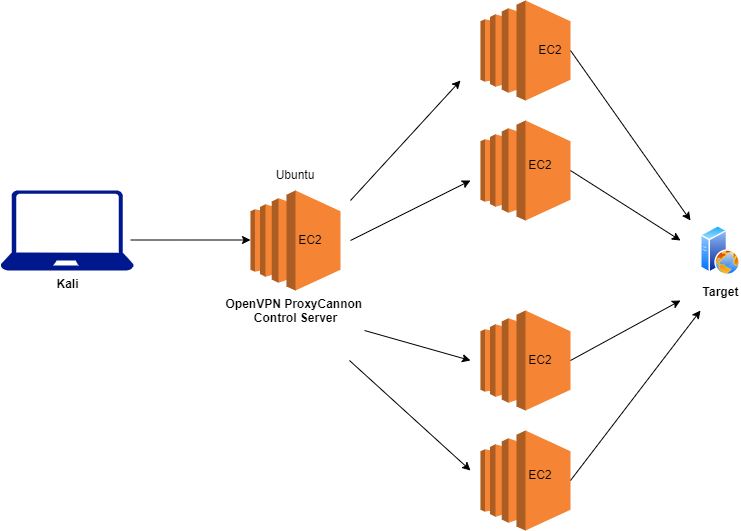
In this blog, we will focus on ProxyCannon-NG: https://github.com/proxycannon/proxycannon-ng
ProxyCannon-NG is proxy tool that leverages cloud environments giving a user the ability to source (all) your traffic from an endless supply of cloud based IP address. Think of it as your own private TOR network for your redteam and pentest engagements. No more defenses throttling and blocking you!
1. Spin up EC2 Ubuntu 18.04 Instance
Instance type: t2.micro (By default selected)
Name your key pair: proxycannon
Security Group: Allow All Traffic from Anywhere

2. Create a new IAM user with "Programmatic Access" so proxycannon control server can create EC2 nodes:
Assign "AmazonEC2FullAccess" permission to this IAM user

We will use "Access key ID" and "Secret access key" later.
3. Configure SSH on Kali
mkdir ~/.ssh
mv proxycannon.pem ~/.ssh/
chmod 600 ~/.ssh/proxycannon.pem
gedit ~/.ssh/config
Host proxy-controlserver
HostName 100.26.188.186
User ubuntu
PubKeyAuthentication yes
IdentityFile ~/.ssh/proxycannon.pem
StrictHostKeyChecking off
4. Installing proxycannon-ng
ssh proxy-controlserver
sudo -i
cd /opt/
git clone https://github.com/proxycannon/proxycannon-ng
vi proxycannon-ng/nodes/aws/main.tf
# replace EC2 "region" with proxycontrol ubuntu EC2 region
# replace EC2 "ami" with proxycontrol ubuntu EC2 AMI id
# replace "instance_type" also based on your ec2 instance

# setup aws credentials
vi /root/.aws/credentials
[default]
aws_access_key_id = AKIAS7U4XXXXXXXXXXXXX
aws_secret_access_key = Ux25n4YFi4XXXXXXXXXXXXXXXXXXXXXXX
region = us-east-1
# copy proxycannon.pem SSH key from kali to proxycannon control server
scp ~/.ssh/proxycannon.pem proxy-controlserver:/home/ubuntu/.ssh/proxycannon.pem
# In our SSH session on the Proxycannon Control Server, copy the SSH key to the root user's ".ssh" directory and confirm that the file has the proper permissions:
cp -v /home/ubuntu/.ssh/proxycannon.pem /root/.ssh/
chown -R root:root /root/.ssh
chmod 600 /root/.ssh/proxycannon.pem
# Edit "variables.tf", Replace "subnet_id" with proxycannon control server EC2 subnet ID, and Change "count" to the number of EC2 nodes you want to spin up
vi /opt/proxycannon-ng/nodes/aws/variables.tf

# Installing AWS teraform provider
cd /opt/proxycannon-ng/nodes/aws/
terraform init
terraform apply

Here we can see, we spin up 2 EC2 instances. We can go for more also, more instances more ips ;)
5. Copy OpenVPN client files to kali and connect using openvpn
On Proxycannon control server:
mkdir /home/ubuntu/client-files
cd /etc/openvpn/easy-rsa/keys/
cp -v ta.key ca.crt client01.[ck][er]* /home/ubuntu/client-files/
cp -v /root/proxycannon-client.conf /home/ubuntu/client-files/
chown -R ubuntu /home/ubuntu/client-files
On kali:
scp -r proxy-controlserver:~/client-files ~/
cd ~/client-files
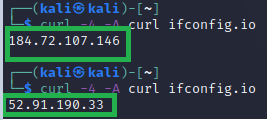
sudo openvpn --config proxycannon-client.conf
6. Destroying all exit nodes
sudo su
cd /opt/proxycannon-ng/nodes/aws/
terraform destroy
If you are blue teamer, as you can see if you deny the adversary the use of one of their IPs, they can usually recover without even breaking stride. Its better to focus on understanding attackers Tactics, Techniques, and Procedures (TTP) and prevent him/her at this level.